How to protect the Windows Remote Desktop
Exposing on public network, internet, your own Windows or one of the corporate servers via Remote Desktop, could be a must … Inevitable. However, there may be problems with unauthorized access/intrusion. Our Remote Desktop could thus turn into a very dangerous Trojan horse for the entire internal network.
How do I know? How can I protect the server?
That's what we're going to talk about.
- What to check
- How I protect my Remote Desktop
- Firewall to protect remote top desk
- General advice
What to check
To monitor access logs, for any suspicious activity, you should know that system accesses are tracked in the event viewer (eventvwr). By searching for the event with ID 4642 we will be able to analyze the logins performed over time.
Time is a key factor when you suspect an intrusion, in fact, the log is usually overwritten very quickly. So look at its size.
How to see events.
To access Event Viewer with the Windows interface you can go to Control Panel. So:
System and Maintenance > Administrative Tools > Event Viewer.
Filtering by ID 4642 you will be able to have all the information we are looking for.
How I protect my Remote Desktop
Here is a list of only 4 points to effectively protect your remote desktop.
- Password policy. Strong passwords and change mandatory at least every 90 days.
- Here's how to d
o it:https://docs.microsoft.com/en-us/previous-versions/windows/en-pro/windows-server-2003/cc781633(v-ws.10)?redirectedfrom?MSD
N For example with Local Security Policy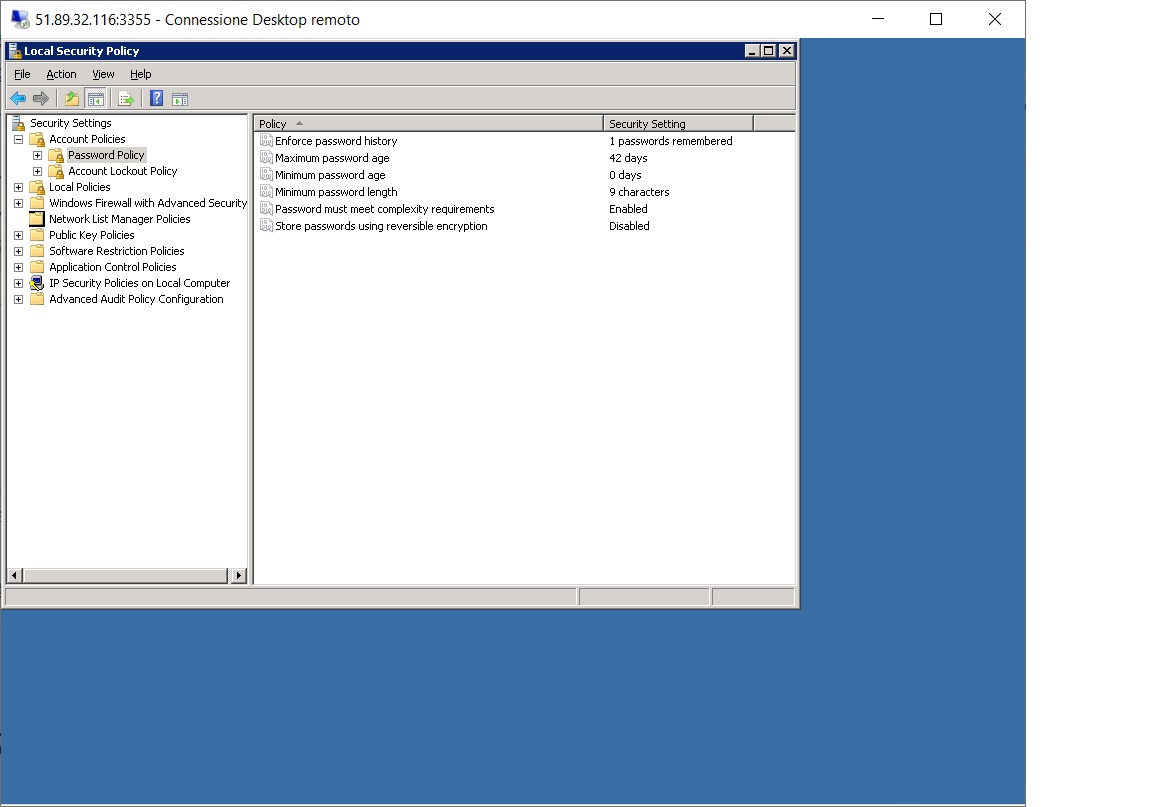
Then we will certainly have to force users to change their passwords the first time.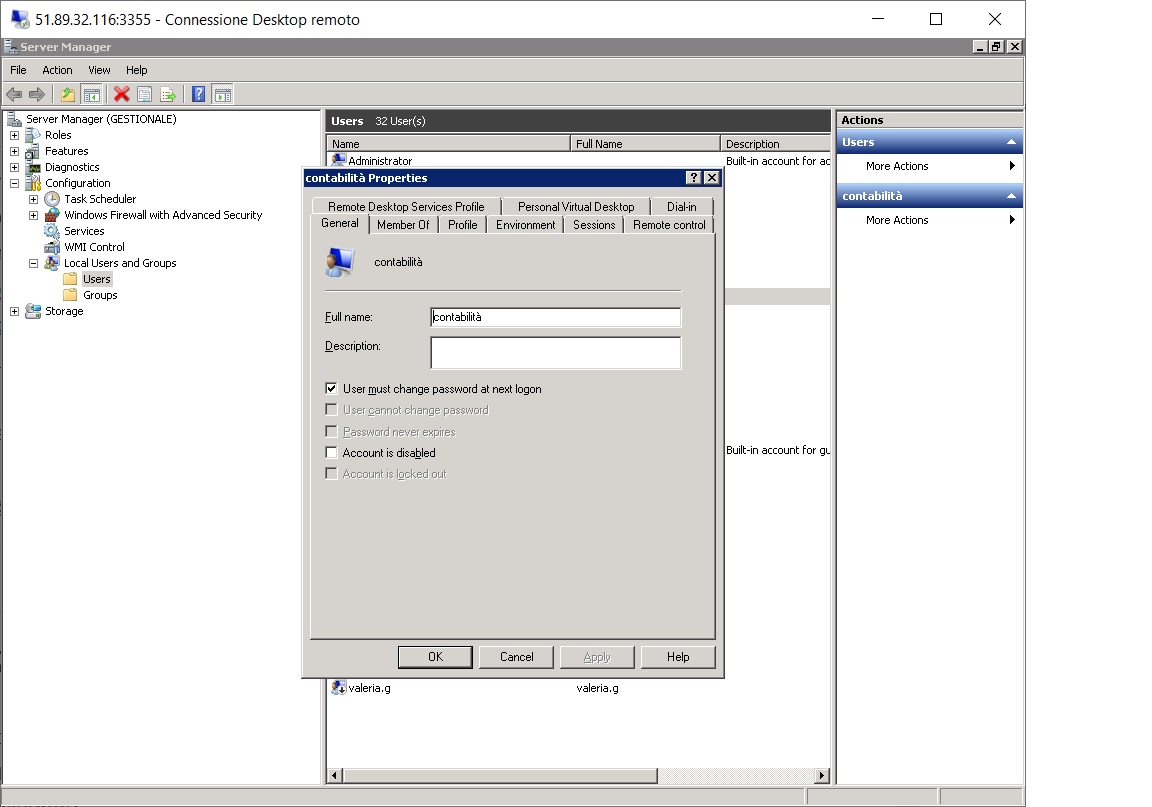
- Here's how to d
- Limit the maximum number of failed logins per account.
- Also in the Local Security Policy, the Account Policies>Account Lockout Policy are placed. Here you can set the lockout threshold. I'd put in a maximum of 4 attempts.
- A lot of attention! If it is your account that gets blocked … think about the consequences.
- Do not allow remote access to users who belong to the "administrators" group.
- Do not allow remote access to users in the "everyone" and "guest" group.
For steps 3 and 4 I recommend that you read the https://techcommunity.microsoft.com/t5/ask-the-performance-team/8220-allow-logon-through-terminal-services-8221-group-policy-and/ba-p/374961 article carefully
Firewall to protect remote top desk
We will definitely have a firewall upstream of our Windows host, through which we will have set rules to expose in our Desktop. You should:
- Set rules to restrict access to only authorized IPs.
- Set any time-based rules (typically a desktop is used to work during business hours).
- Evaluate for external access, VPN technology.
If you don't have an upstream firewall, you can, as a last resort, use the Windows firewall.
General advice
In the end I can advise you to reflect on these simple points.
- Isolate the server. If you need to access other systems, I recommend that you do not store passwords for accessing other systems on the network.
- Update your operating system with the security patches offered. Needless to say, patches are also not always solutive: this point, if applied alone, can be completely ineffective.
Comments? Do you want to discuss something? Write below or contact me by any means. Hello!

